Windows OS, by default has Windows account lockout security feature enabled, which locks account in case too many failed login attempts. As there is many automatic bots running inside infected servers and computers which automatically scans IP subnets ranges RDP 3389 port and performs brute-force passwords attacks, Windows account can be temporary locked by the system to prevent brute-force attacks. After some time account will be automatically unlocked, but may be locked again if brute-force attack continues.
To prevent automatic account locking we recommend to disable this feature in Windows OS:
1. Login inside your Windows server RDP connection.
2. Open Local Security Policy: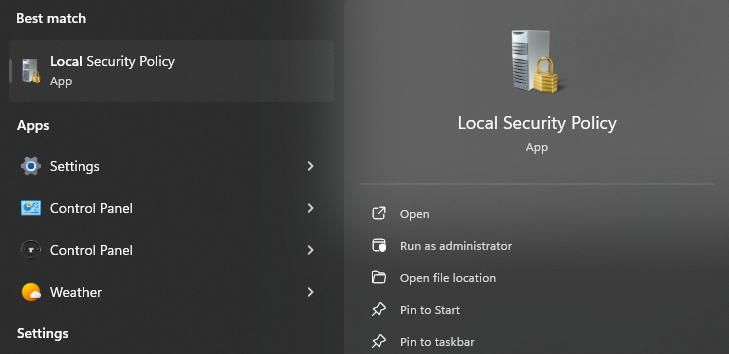
3. Click on Account Policies -> Account Lockout Policy: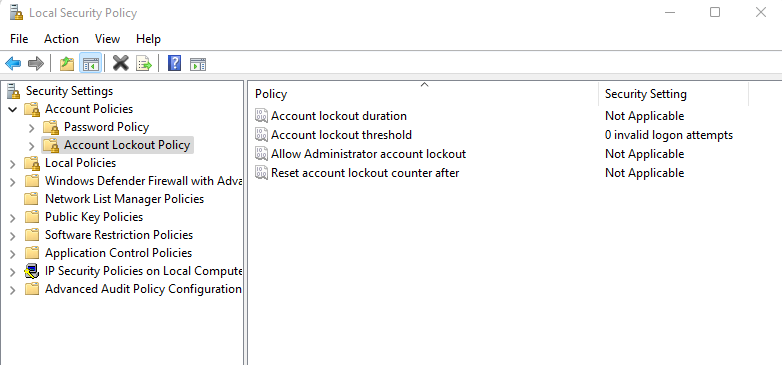
4. Click on Account lockout threshold and change it to 0: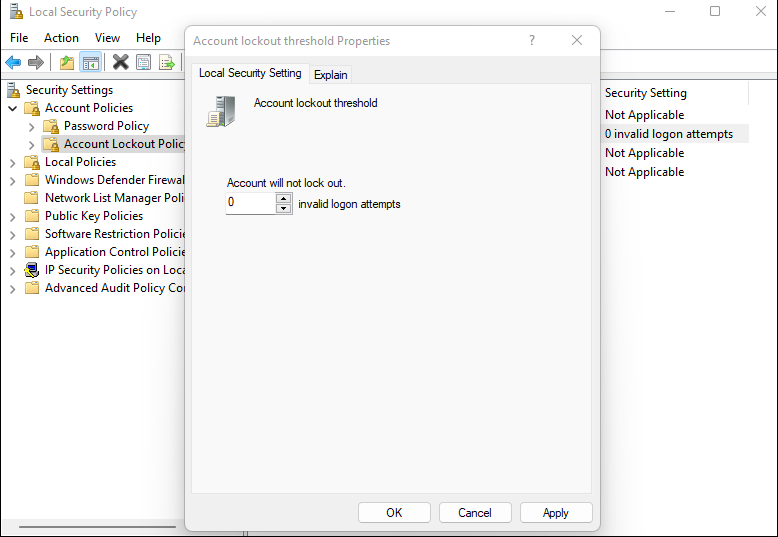
5. Click Apply and then OK buttons for changes to take effect.
After automatic account lock out disabling your Windows account will not be locked.
Important! Please always use strong and secure passwords to prevent brute-force attacks, weak password guessing and server hacking.
